FileRepMalware is the cyber threat of different PUP-to-Trojan functionalities. This name is often referred to as Win32:Evo-gen. Avast and Avg AV engines most commonly report on the possible danger of a file or website. In most cases, antivirus terminates the threat and reports about the already eliminated intruder. It is linked to unsafe KMSPico installations and like applications that can enable programs without the developer’s knowledge.
There is a major risk of this malware being on the system itself as a virus and proliferating Windows systems. Since different commercial contents have been detected on the screen due to this infection, the FileRepMalware virus is suspected to be a PUP. Other virus-related identification names have trojan features and potential danger to your system. You should not disregard the notifications and clean the system using the AV.
What is FileRepMalware?
The FileRepMalware virus is believed to be a Trojan Horse. It is one of the generic detections, which means that the antivirus does not know the exact behavior of the file; it classifies it as potentially malicious due to abnormal traits and automatically immunizes it. Besides, the file’s popularity also appears to be significant.
The FileRepMalware, Win32:Evo-gen, can also include a technical reference, which means the file reported is part of the Windows system. At the same time, the Evo-gen suggests a general Trojan style classification of files.
When the antivirus returns a warning recommending FileRepMalware PUP elimination, all certified security experts promise to do so immediately. This software (PUP) or file, possibly unwanted, was spread using a false KMSPico app. Subsequently, an adware application can be imported to the device. Thus the malware can open the back door and run other malware on the device (adware, browser hijacker).
| FileRepMalware | |
| Alternative name | Win32:Evo-gen [Susp] |
| Detection | Avast, Avg |
| Related to | KMSPico |
| Category | Adware/ trojan horse |
| Prevention tips | Avoid possible infections of adware or malware by taking control of your downloads (Custom configuration), preventing visits to third-party pages, and installing reputable anti malware on your machine |
| Main dangers | Can be used to infect the system with malware; can steal personal information |
| Removal | Delete FileRepMalware automatically using anti-malware program, repair system with Reimage |
Should I Remove FileRepMalware?
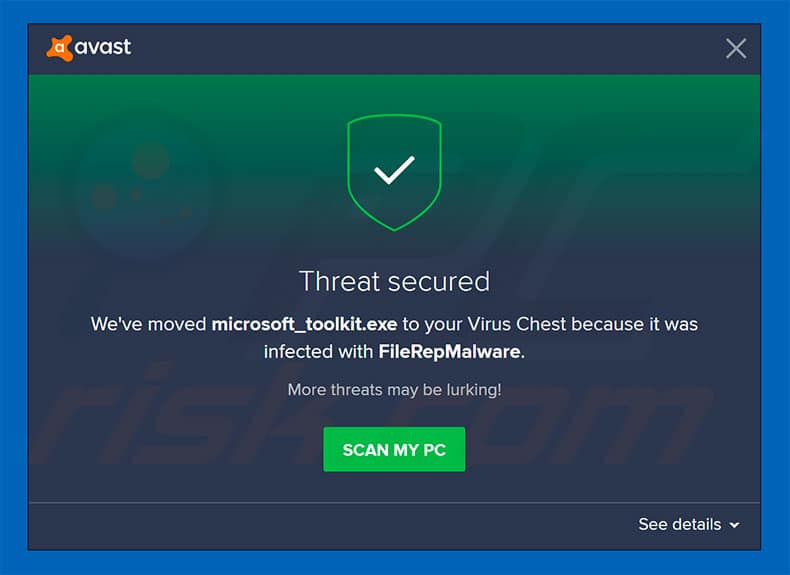
To avoid suspected malware activities, you should start deleting FileRepMalware ASAP. If you have been alerted of this threat by your antivirus, end it without a doubt. Additionally, with Reimage or another reliable security method, repair the damage caused by this malware. Many that have not previously handled malware should know these facts:
- Advertising malware will cause actual system damage. Adware systems produce an excessive number of third-party ads in such intrusive ways as pop-ups, banners, or interstitials.
- Malware inserted ads can cause redirects to be suspicious or harmful websites.
- Malware programs can hijack web browsers. In other words, the current tab’s home-page search provider, URL, and compromised search results may be overridden.
- The FileRepMalware virus can also be used to monitor people’s browsing activities using cookies or other small files. Tracking cookies typically capture certain pieces of information or confidential data, including IP address, email address, geo-location, name, etc.
Unfortunately, more upgraded and dangerous malware can remove files from your machine or add new suspicious data to the device to ensure that the key virus stays persistent and hard to delete. A repetitive error appears on the screen, and some applications are shut down out of nowhere when the FileRepMalware virus is detected on the device.
You must concentrate on eliminating FileRepMalware because slow computing speed is just the beginning of irritation and potential harm to your system caused by this threat. If you save your personal information on your computer, the malware will reach it and even use it in other scams when you get fake emails or strange phone calls.
Ensure that you uninstall FileRepMalware with a reliable anti-malware tool and suggest programs other than those that show double-checking errors. Repair tools such as Reimage will also boost efficiency by cleaning up potential virus damage and repairing problems.
How did adware install on my computer?
The most frequent distribution of potentially unwanted programs includes the disruptive ads described above and a misleading marketing strategy called “bundling” In general, adware infiltrates systems without approval because of lack of awareness and reckless actions of some users. Bundling is the stealthy download of third party applications together with regular software/apps. Developers do not disclose these installations properly.
They hide “bundled” applications in “Custom/Advanced” download/installation settings (or other sections). Research reveals that a substantial number of users are clicking suspicious ads and skip download/installation. This action also allows potentially unwanted applications to be installed unintentionally.
Avoid the installation of potentially unwanted applications
Be cautious when surfing the Internet and especially when using software to avoid device intrusion by PUPs. Cybercriminals spend a lot on intrusive advertising design. Thus, most of them appear legitimate. Once clicked. However, they redirect to gambling, adult dating, pornography, and other suspicious websites. If you encounter such redirects, uninstall all suspicious software and browser plug-ins immediately.
Also, check each download/install dialogue window and opt-out of any additional apps. It is advised that the applications only be downloaded directly from official sources. It is also important to use a legal anti-virus/anti-spyware suite. Caution is the key to computer security.
Steps To Follow To Remove FileRepMalware
Remove FileRepMalware from Windows systems
Remove all potentially unauthorized programs from the Control Panel if you want to attempt to uninstall FileRepMalware manually. Also, check all Windows and Windows System folder and HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run folder in Windows Registry:
To remove FileRepMalware from Windows 10/8 machines, please follow these steps:
- Enter the Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
- In the uninstall programs window, look for any potentially unwanted programs, select these entries and click “Uninstall” or “Remove”.
Steps for Windows 7/XP
- Click on Windows Start > Control Panel located on the right pane (if you are a Windows XP user, click on Add/Remove Programs).
- In the Control Panel, select Programs > Uninstall a program.
- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Steps for Mac OSX users
Click Finder, in the opened screen select Applications. Drag the app from the Applications folder to the Trash (located in your Dock), then right click the Trash icon and select Empty Trash.
Scan the computer for any remaining unauthorized components or suspected malware infections after uninstalling the potentially unwanted program that causes FileRepMalware to be redirected. Use the suggested malware removal tool to scan your computer.
Remove FileRepMalware from Internet browsers
Internet Explorer

If you noticed an excessive amount of advertisements when browsing, remove PUPs and potentially malicious files and then reset your web browser.
Remove dangerous add-ons:
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser.
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for FileRepMalware and other suspicious plugins. Click on these entries and select Disable.
Change your homepage if it was altered:
- Open IE and click on the Gear icon.
- Select Internet Options.
- In the General tab, delete the Home page address and replace it with your preferred one (for example, Google.com).
- Click Apply and then select OK.
Delete temporary files:
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete
- Select relevant fields and press Delete.
Reset Internet Explorer:
- Click on Gear icon > Internet options and select Advanced tab.
- Select Reset.
- In the new window, check Delete personal settings and select Reset again to complete FileRepMalware removal.
Google Chrome

- Click the Chrome menu icon Google Chrome menu icon (at the top right corner of Google Chrome), select “More tools” and click “Extensions”.
- Locate all recently-installed suspicious browser add-ons, select these entries and click the trash can icon.
If you continue to have problems with removal of the filerepmalware infection, reset your Google Chrome browser settings.
- Click the Chrome menu icon Google Chrome menu icon (at the top right corner of Google Chrome) and select Settings.
- Scroll down to the bottom of the screen and click Advanced.
After scrolling to the bottom of the screen, click the Reset (Restore settings to their original defaults) button.
In the opened window, confirm that you wish to reset Google Chrome settings to default by clicking the Reset button.
Mozilla Firefox

Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select plugins that are related to FileRepMalware and click Remove.
Clear cookies and site data:
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
In case FileRepMalware did not get removed after following the instructions above, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.
- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox – this should complete FileRepMalware removal.
Microsoft Edge

Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the FileRepMalware-related extension and click on the Gear icon.
- Click on Uninstall at the bottom.
Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.
Reset MS Edge if that above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.
If this solution fails to help you, you need to use an advanced Edge reset method. Note that you need to back up your data before proceeding.
- Find the following folder on your computer: [C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.]
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete
- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
- Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” –Verbose
Chromium-based Edge

Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove
Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.
Safari

Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension related to FileRepMalware and select Uninstall.
Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.Clear cookies and website data from Safari
Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop, and then select Empty Caches.
How to Guard Against Malware Attacks
Here are ten fundamental security guidelines to assist you in avoiding viruses and securing your device:
1. Use a reliable antivirus program and update it on a regular basis.
To stay on top of the most recent cyber threats, it’s critical to use a high-quality antivirus and always keep it up to date. Malwarebytes Premium is a favorite of ours, and we use it on all of the devices, including Windows and Mac desktops, as well as mobile devices.
Malwarebytes works alongside your existing antivirus software, closing in any gaps in its defenses and giving added security against sneakier security threats.
2. Maintain current software and operating systems.
Maintain the most recent versions of your applications and operating system when an update for your device is available, download it, and set it up immediately away. Security enhancements, vulnerability patches, as well as other critical maintenance are frequently included in these updates.
3. Exercise caution when downloading and installing programs and applications.
When installing software, pay special attention to the installation windows and license agreements. Custom or sophisticated installation options frequently reveal any 3rd-party software that is also installed. Take your time at each step of the process to ensure you understand what you’re committing to before clicking “Next.”
4. Get an ad blocker.
Utilize a browser-based content blocker, such as AdGuard. Content blockers aid in the prevention of dangerous advertisements, Trojans, phishing, and other unpleasant content that even an antivirus program alone may not be able to detect.
5. Be cautious of what you download.
The primary goal of cybercriminals is to lure you into installing malware-infested programs or applications that contain viruses or attempt to steal information. Such malware can be camouflaged as an app, anything from a famous game to a traffic or weather app.
6. Be on the lookout for those attempting to deceive you.
Always be aware and on the lookout for anyone attempting to fool you into clicking on links or responding to messages, whether it’s through email, smartphone, messenger, or other applications. Remember that phone numbers are easily spoofable, so a recognized name or number does not guarantee more trustworthy messages.
7. Make a backup of your data.
Back up your data regularly and ensure that your backup data can be retrieved. This can be done manually on an external hard drive/USB stick or automatically with backup software. This also is the most effective technique to combat ransomware. Never attach a backup disk to a computer that you suspect is compromised with malware.
8. Select strong passwords.
For each of your accounts, choose strong and unique passwords. Passwords should not contain any personal information or words that are easily guessable. When possible, activate two-step authentication (2FA) on all accounts.
9. Take caution where you click.
Use caution whenever you click on links or download attachments from unknown sources. These could carry malware or phishing schemes.
10. Avoid using pirated software.
Avoid using P2P file-sharing tools, keygens, crackers, and pirated software, which can frequently jeopardize personal data, privacy, or both.
To avoid possible dangers online, adhere to these ten basic safety principles. When you do so, you can prevent a lot of the nasty surprises that can occur when surfing the internet.
Summary
Commonly, adware or potentially unauthorized programs penetrate Internet browsers through free software downloads. Note that the safest source for downloading free software is from developers’ websites only. Be very cautious when you download and update free applications to prevent adware installation. Choose the custom or specialized installation options for the installation of previously downloaded free programs – this move exposes any currently unused install-listed applications along with your freely selected program.
Read Also
- How to Change Your Account Name on Windows 10
- What is AppVShNotify & Why Should We Disable it?
- Antivirus vs Internet Security
- Malwarebytes vs Avast
- 7 Tips to Keep Your Computer Secure
- TotalAV Review 2020
- 7 Solutions To Fix SD Card Recognized On Windows
- How to Change a File Extension in Windows
- How To Fix “Steam Content File is Locked” Error
- What is ASP.NET Machine Account & Should it be Deleted?
- How to Disable Adobe AcroTray.exe from Starting at Startup
- What is Vulcan Runtime Libraries And Do I Need It?