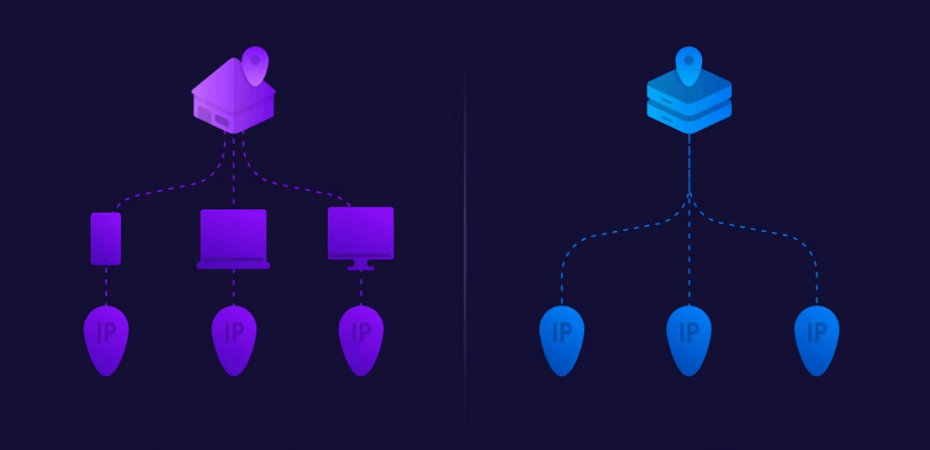
A data center proxy, like any proxy, bridges the gap between an internet-connected device and the website accessed. The gateway software switches the access point’s IP address when connecting to the internet with one temporarily obtained from a physical data center. By doing this, the proxy user gains a high level of anonymity and may even be able to control how they seem on the page they are accessing.
Datacenter proxies are physically different from home and mobile proxies. A data center proxy’s IP addresses come from a data center full of servers rather than a physical address or a number from a cloud of mobile IPs. This is similar to all proxy services substituting or concealing an original IP address with another IP. This frequently results in data center proxies running faster and with reduced latencies.
This form of proxy effectively gives a user a new location by adopting the IP address of a data center, and it can be used for both good and bad activities behind the disguise.
How Do Data Center Proxies Work?
Using some of the best data center proxies you can get many benefits, but before digging into the pros, you must learn how these proxies work and the effort that goes behind them. These proxies work like any other ordinary proxy:
- User installs a proxy’s gateway software on their devices, such as mobile phones or laptops.
- The minute the user gains access to the internet, the device immediately connects with the data center.
- There it gets assigned an IP address from one of the servers at the data center.
- Using the new IP address, the user can easily navigate to different websites as an anonymous user.
- Remember that this process can only be done on a device with the installed software.
You will find multiple companies on the internet that offer this service with a subscription model through which you can lease addresses, especially for users who require numerous IPs. Some companies also provide the services for free, but that’s usually for one-time users. It’s best to go for the paid model to avoid issues with the IP addresses.
Types of Data Center Proxies

Some of the popular data center proxies include the following:
1. HTTP or Hypertext Transfer Protocol Proxies
The Hypertext Transfer Protocol Proxies are used for surfing the internet. The most common part of the HTTP browsing experience is entering the URL or clicking on it. This is then submitted to a server hosting the website. When the user requests, the server responds to the information the website provides. This setup is popularly known as the client-server model, where users send a request to a server, and they then respond to it. The HTTP is a middleman between the server and the user’s web browser.
2. Secure Socket Proxies or SOCKS
SOCKS is a proxy service that sends multiple network packets to and from the server to the user’s browser and vice versa. HTTP proxies are used to acquire a website’s information, but SOCKS comes in handy for different applications. Their level of proxies is less than an HTTP. The network protocol followed by SOCKS allows other users to communicate with multiple servers but through a firewall. It can handle traffic from any protocol or program and directs network traffic to the proper server.
Apart from these proxies, multiple other proxies exist. These proxies are designed to fit personalized needs to help users overcome problems, and it is essential to be aware of each of them.
- Residential proxies
- Forward proxies
- Mobile proxies
- Reverse proxies
- Anonymous and elite proxies
- Public, shared, and private proxies
- Rotating proxies
- Transparent proxies
How Can a Data Center Proxy Help You?
Here’s a zoom-in on the uses of proxies, specifically data center proxies.
Clouding Identity
A range of privacy-protecting methods, including VPN and Tor, are used in identity obscuring. The objective is always to conceal the usage of privacy protection applications to make it seem like it is not being used, even though the basic obfuscation technique varies from tool to tool.
Datacenter proxies are essential for people living in nations where VPN use is restricted since they allow users to dodge VPN-blocking software. It is also an easy fix if you have difficulty with an internal network that does not support VPN.
So many users in different parts of the world are restricted and need access to some platforms, such as from China, Israel, Iraq, etc. They impose limitations on some websites, and data proxy software can help overcome and bypass these VPN bans.
Sidestepping Location-Based Restrictions
Multiple companies choose to block different regions or countries to avoid massive network traffic on their website by applying geo-location restrictions. For instance, an e-commerce site might disable other users meanwhile only enable Chinese users to purchase and sell from their website. These location-based restrictions ensure the website speed is improved for users for its targeted audience. But by using a data center proxy, users can access the website and sidestep the located-based restrictions.
Extraction of Data and Collection of Information
A data center proxy can conceal the IP address of a user’s web scraping machine so they can get information from a website without disclosing their IP address. Since it sees the request coming from the IP address of the proxy device, the target site is unaware of the IP address of the initial local scraping machine.
The data center proxy can get around website limitations if a user wants to visit a website from another country without revealing their IP address. Also, users can dodge rate limitations on their desired website very easily.
In Short
In this era of technology and digitalization, data center proxies can be seen around you and are used by so many users. They are convenient, hide your IP addresses, and have no link with your internet connections. In short, they’re entirely self-contained and are the perfect helping hand whenever you want to access restricted websites because they simplify the process.
Read also: