Cyber security refers to the practice of guarding our computers, mobile phones, electronic devices, and data from being struck from malign and harmful attacks. There are various categories of cyber security, applicable differently on different systems. Such as, Network cyber security is practiced for securing the network from unknown intruders. Whereas, Information security protects the privacy of data either stored or in progress.
Why journalists need cyber security
In the field of journalism, you need to be more cautious about the security of your data to be published and identities incorporated. Most of the time, leaked data causes huge scandals of defamatory. In some cases, the witness/person does not want his identity to be revealed due to privacy or security reasons.
Due to the increase in the number of journalists, professional rivalry is common nowadays. In the case of poor cyber security, competitors may take advantage of cunningly of the data theft/hacked.
Globally, following is the chart of the highest and lowest number of malware attacks by country (As per sources)
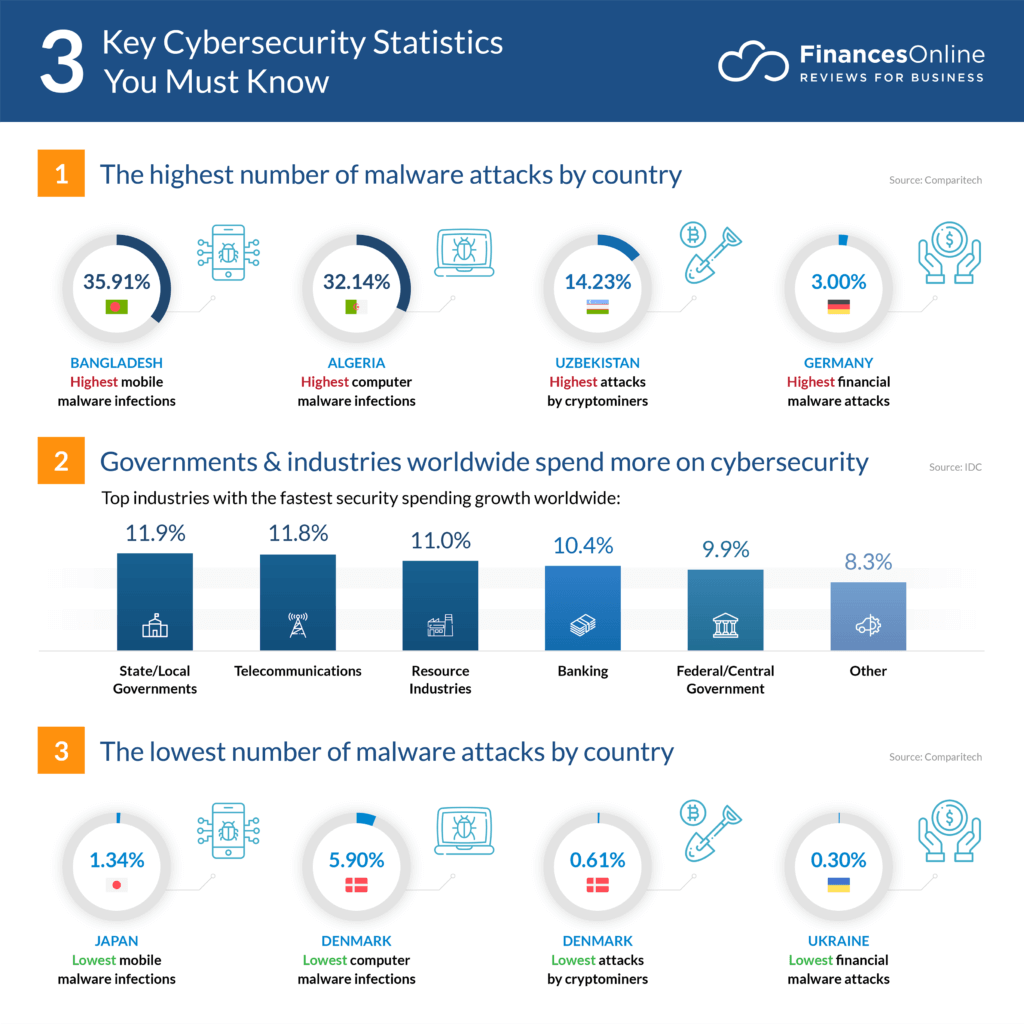
All the malware attacks are results of poor cyber security.
Most Common Kinds of Cyber Security Threats
Cyber security experts are well-versed in the following forms of cyber security threats.
1. Malware
Malware is defined as malicious software, which includes spyware, ransomware, viruses, and worms. Malware is triggered whenever a user clicks on a malicious email attachment or link, which causes harmful software to be installed. According to Cisco, once activated, malware can:
- Access to critical network components is restricted (ransomware)
- Install additional malicious software.
- Obtain information covertly by transferring data from the hard drive through spyware
- Disrupt individual components, rendering the system unusable.
2. Emotet
Emotet is described by the Cybersecurity and Infrastructure Security Agency (CISA) as “an advanced, modular banking Trojan that primarily serves as a downloader or dropper of other banking Trojans.” Emotet remains among the most expensive and damaging malware.”
3. Denial of Service
A denial of service (DoS) assault is a sort of cyber attack that overloads a network or computer, rendering it unable to respond to requests. A distributed denial of service (DDoS) assault does the same objective, but the attack begins on a computer network.
Cyber attackers frequently use a flood attack to interrupt the “handshake” procedure and conduct a DoS. Other approaches may be utilized, and some cyber attackers could use the time while the network is down to launch further attacks. Jeff Melnick of Netwrix explains a botnet is a sort of DDoS during which millions of devices can be compromised with malware and manipulated by a hacker.
Botnets, also known as zombie systems, attack and overwhelm a target’s processing capacity. Botnets are located in different parts of the world, which makes them difficult to track.
4. Man in the Middle
When hackers inject into a two-party transaction, this intrusion is known as a man-in-the-middle (MITM) assault. According to Cisco, they can select and take data after disrupting communications. MITM attacks are common when visitors connect to an unencrypted public Wi-Fi network. Attackers position themselves in the Middle of the transaction between the network and the visitor, then utilize malware to install software to manipulate data.
5. Phishing
Phishing attacks use phony communication, like an email, to deceive the recipient into opening it and following the instructions, such as submitting a credit card number or installing malware on the victim’s device.
6. SQL Injection
A Structured Query Language (SQL) injection is a form of cyber attack that occurs when malicious code is inserted into a SQL server. When a server is infected, it releases data. Entering the malicious code into a susceptible website search box might be as simple as that.
7. Password Cracking
A cyber attacker can easily gain access to a lot of information with the appropriate password. Data Insider defines social engineering as a “tactic cyber attackers utilize that depends primarily on human connection and frequently entails luring people into breaching basic security standards.” Entering a password database or guessing are two other sorts of password assaults.
STATISTICS OF RISE IN CYBERCRIME IN PAST 5 YEARS
The importance of cyber security gained ultimate limelight in the last few years due to the express increase ratio of successful attacks on online stored data.
Have a look at these statistics of cybercrime rise 2015-2019
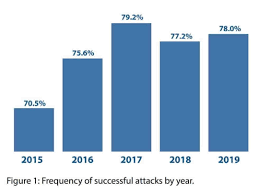
This bar chart shows a comparison of successful cyber attacks in the last 5 years.
Being a journalist, you should always imply your digital safety kit for securing your privacy, data, and information from cyber thieves and hackers. Your digital security kit includes the following:
Methods of Cyber Security
Being a journalist, you should always imply your digital safety kit for securing your privacy, data, and information from cyber thieves and hackers. Your digital security kit includes the following:
- Protect your accounts
- Defend your accounts from Phishing attacks
- Adapt toolkit to secure Your device
- Encrypt communication
- Cyber security while traveling abroad
- Cyber security through social accounts and web browsers
Protect your accounts
Nowadays, journalists use different online platforms and account for saving their data. This data includes not only personal or work-related information but also sources. These accounts need to be protected wisely. Leak or loss of this data can lead to problematic situations. In order to protect your account you should:
- Keep your privacy settings as strict as possible.
- The visibility of your data to viewers should be limited. You need to restrict your public look of account (especially in the case of social media accounts).
- Delete such accounts that have your data inside but are no longer in your use.
- Try making secured backup copies of your private date of accounts like important messages and documents. You may save these back up in your Cloud and flash device.
- Create unusual, long, and unique passwords. Accounts with easy passwords are more likely to be hacked.
- Keep a keen eye on your account’s activity. Never ignore the suspicious movement.
Defend your accounts from Phishing attacks

As a journalist, in order to maintain your cyber security, you have to play defensive with phishing attacks. The first need is to understand what phishing attacks actually are?
It is a kind of cyber attack that aims to steal the user’s data. Greeting emails are one common form of a phishing attack. It aims to collect your login information, credit card number, and access to your private data.
These attackers makes the user believe that they are approaching from an authentic source and asking your information for any legal or important purpose.
Be aware of such unknown messages and mails which asks you to do something really quick. Do not download attached files or click redirected links without authentication of them being true. Such redirected links and downloads are malware attacks on your security system.
Stay more attentive to phishing attacks when anyone around you knows that your account is holding important data that can be misused.
Adapt Toolkit to secure your device
Your device holding your online working accounts and significant data must adapt the security tool kit. This security tool kit includes:
- Apply biometric identification security to your device.
- Keep customized pin codes/ patterns/ Long passwords which are not easier to break.
- Ensure your connectivity to WLAN is secured.
- Disable your device’s hotspots/ Bluetooth/ and other connection methods with other devices when not in use.
- Download Antivirus applications or software on your device to fight malware attacks and viruses. Keep these softwares and applications updated and active.
- Avoid connecting your device to transferable devices.
- Use VPN for browsing if you are unsure of the network security of the website.
- Avoid entering websites and links, about which your device notifies you could be harmful.
- Do not leave your device unattended in public places.
Encrypt Your Online Communication

To be more secure as a journalist, try encrypting your communication. Use an encrypted messaging app and emails. You must have a sound knowledge about the messaging app you are using that where the communicated data is stored and backed up.
Your communicated contacts should be synced to your device for backup reasons. Choose authentic and well-known email encryption software to encrypt your conversation done via emails. Email addresses of the sender, receiver, and title of the email does not need to be encrypted.
Use encryption software regularly to be in practice. Keep updating this communication encryption software and apps for cyber security development.
Develop security of Internet

Use your internet connection securely. Make sure your privacy sharing applications and services are switched off while using the internet.
Download Privacy Badge to defend privacy-invading advertisements and website links. Reduce the range of your wireless connection to limit accessibility for other people. Create a unique password for your internet connection.
Cybersecurity While Traveling Abroad

If the journalist is a frequent traveler, then he must take some precautions in the context of cyber security when crossing the border. A journalist needs to update and change his installed anti-virus software and apps (in case that software is inaccessible in that country). A journalist must accompany his device in which all the data is possessed. Data should be compressed enough that it does not exceed the storage of the device.
Disable location service, so no one can trace where have you taken your data storage device. Avoid using public WIFI.
Disable connectivity of your hotspot or Bluetooth or any else privacy sharing medium.
Web Browsers And Social Account Security

If you are one of the frequent social media users, then you are more likely to be attacked by hackers. In the field of journalism, you should never publicize your important information and sources. Only professional contact access may be provided.
Many famous web browsers and websites have also come in the limelight when they breached data of its users who took their cyber security lightly.
Do not share contact details and credit card numbers on the websites unnecessarily.
It’s better not to share personal information or any data in regards to journalism cases, persons belonging to these cases, evidence, and sources of evidence.
Journalists, while using a web browser and social accounts, must evolve and explore security features and apply them as strictly as possible.
Conclusion
Not only journalists but also as an individual, we need to follow cyber security toolkit to defend our online data and privacy. In the case of journalism, use the tool kit more vigilantly and specifically because of the existence of important world news and information, which could help solve cases and change public views.
Keep yourselves updated and upgraded enough to aware of new technology and features regarding security aspects of cyber data.
Read Also

